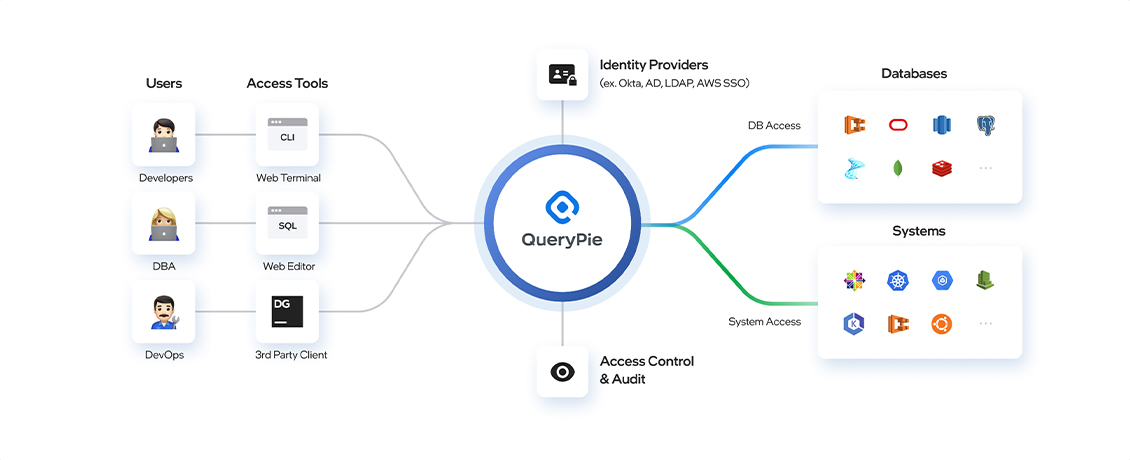
QueryPie
Cloud Data Protection Platform QueryPie is a Cloud Data Protection Platform, CDPP,
that consolidates IT assets such as databases and servers in both cloud and traditional data centers, providing access control and audit support.
It is used by over 70% of domestic unicorns/startups such as Kakao Pay, Kakao Enterprise, Yanolja, Dunamu, Karrot, Musinsa, and Toss to comply with and manage personal information regulations, financial regulations, and compliance.
Challenges with cloud data security
In the era of cloud computing, enterprises face various issues related to data security. The proliferation of vast amounts of data and the complexity of infrastructure make it challenging to apply consistent security measures across all resources. This difficulty can lead to serious problems in business operations, including incidents of personal information breaches.
-
 Vast data & various storage
Vast data & various storagevast amounts of data and diverse storage options
-
 Complexity Infra & Resource
Complexity Infra & ResourceThe challenge of fragmented data and resource management
-
 Employee Departures
Employee DeparturesExposure of personal information due to resigning employees and internal threats
-
 Risk of Privacy Leakage
Risk of Privacy LeakageDecreased customer trust due to the leakage of personal information
-
 Compliance Requirement
Compliance RequirementCompliance adherence in response to strengthened relevant regulations




















 ISO/IEC27001
ISO/IEC27001
 ISO/IEC27701
ISO/IEC27701
 ISO/IEC27017
ISO/IEC27017
 ISO/IEC27018
ISO/IEC27018
 ISO22301
ISO22301
 ISMS-P
ISMS-P
 CSA-STAR
CSA-STAR
 CSA-STAR
CSA-STAR
 PCI DSS
PCI DSS
 GOOD Software
GOOD Software